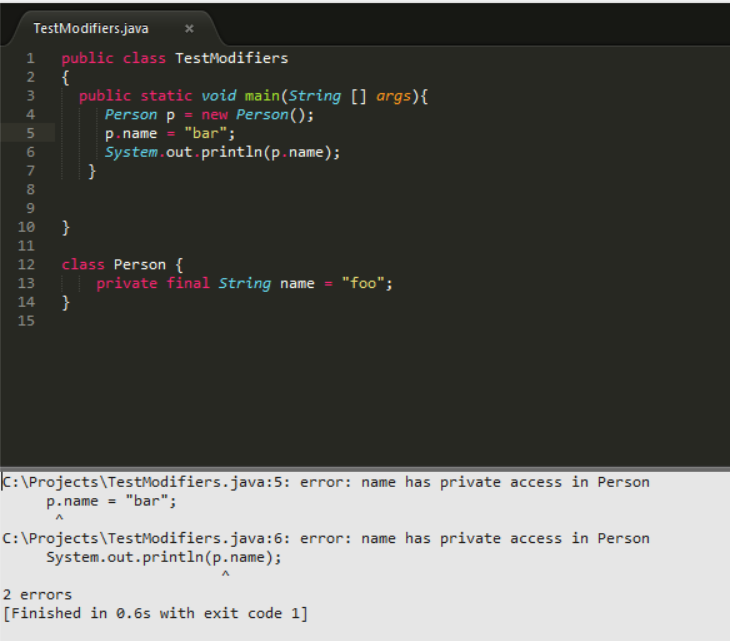
Messaging for the Internet of Things
Messaging for the Internet of Things As we embed processing power to a lot of our everyday things. The thing will need to communicate with a server to send data or get data . The thing needs data in order to make something happen. The thing needs to send data so that we can be smarter on how we use the thing. But How do we send data to a central server that is robust, asynchronous and reliable ? MQ, what is old is new Again MQ or Message Qeueing is new again in the age of the Internet of Things. Messaging Patterns for the enterprise has been around for ages. What were the major reasons that messaging addresses ? 1. Networks are unreliable - data needs to be transported over the network. These networks are a conglemeration of different types of network. Since we do not have control of over most of the network that we use to access the internet. The network will present a lot of problem specially when you are sending messages across the internet. 2. Networks a...