Private final - some things you can't change!
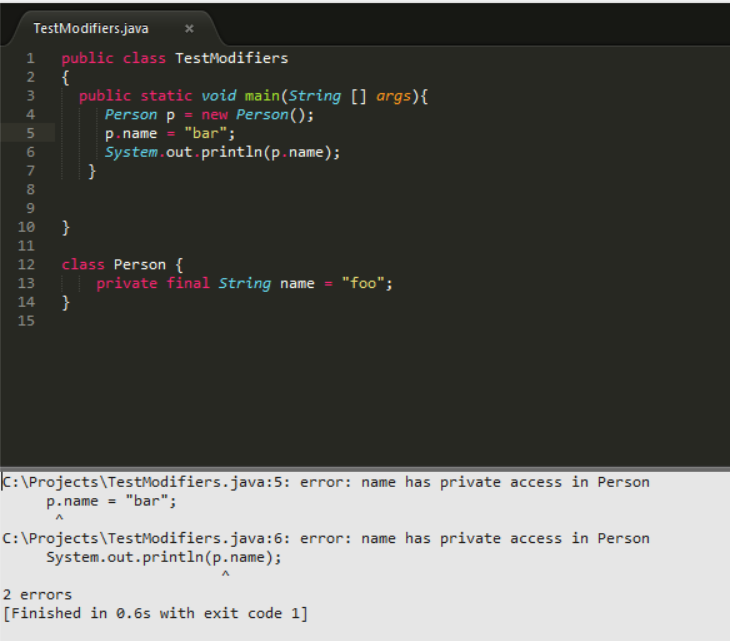
Access ! Access ! For as long as I can remember writing programs in Java. I have used the access modifiers to control access to members of my classes. It is one of the topics in the Certification test in java (SCJP, OCJP). The table below taken from the Oracle Java Tutorials summarizes how each access modifier can restrict or expose a member of your class. Java Access Control Access Levels Modifier Class Package Subclass World public Y Y Y Y protected Y Y Y N no modifier Y Y N N private Y N N N Don't worry it is a private final variable! I can't change its value because it is private final member of the class. Well that is not really true. There is an API for that Java Reflection . The Java Reflection API will allow you to examine and modify runtime behavior of applications in the JVM. "Reflection is powerful, but should not be used indiscriminately". In relation to the access modifiers mentioned above you can disregard it all and do as you please. ...

.png)